Pelion Edge
It is estimated that through 2020, 90% of IoT solutions will use some form of IoT gateway. These solutions come with their own challenges, such as connecting legacy and other devices, the drawbacks of computing at the cloud and security risks. Pelion Edge meets those needs by offering local gateway management, device management for multiple protocols and edge computing. When you combine Pelion Edge with the rest of the Pelion ecosystem, you can use the resulting end-to-end solution from onboarding devices to device management to data collection and management. Pelion Edge is a critical piece of that solution.
 Pelion Edge
Pelion Edge
Solving the challenges you face today
Customers use Pelion Edge to solve the challenges they face today:
- Connecting devices with power, technology, size or security limitations.
- Local device management challenges.
- The time, network bandwidth and cost of computing and analyzing data effectively.
- Security.
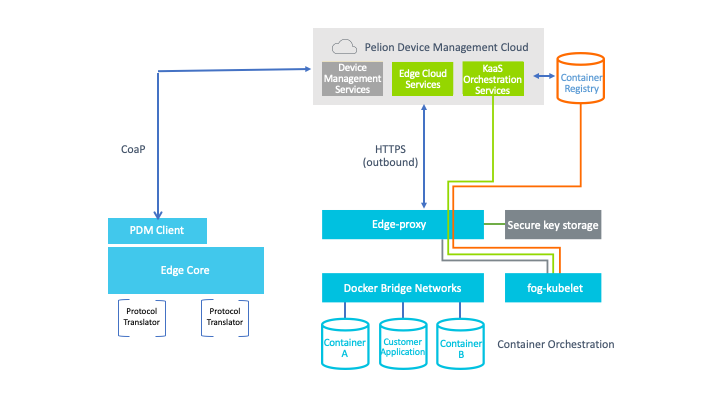
Protocol translation for legacy and constrained IoT devices: Customers come to us to solve the problem of legacy devices in existing infrastructures. Sometimes, these devices use communication protocols that are incompatible with internet protocols (IP), such as BLE, Zigbee, Z-Wave, BACnet and Modbus. With Pelion Edge, we can translate these devices into IP, so you can use the capabilities of the entire Pelion platform, including managing your devices with Pelion Device Management.
Local device management: Pelion Edge supports many features with which you can manage your devices, including device onboarding, first-to-claim, gateway firmware update, resource management (read/write/observe) and local command/control.
Computing at the edge: Pelion Edge hosts applications at the edge and helps those applications manage end devices. This enables you to send only relevant data when computing at the edge, which reduces network overhead and cuts latency, bringing down cloud costs. Because computing occurs closer to the source, turnaround is faster with Pelion Edge, and you can focus on only relevant insights. You can choose only custom applications to be hosted at the edge, so you use only applications that are relevant to your use case. Our reporting capabilities allow you to build your own rich dashboarding and analytics. This enables you to act on only the most relevant insights.
Bedrock of security: End-to-end security is a core part of the entire Pelion platform. This ranges from security at the device, such as support for secure firmware update and management of constrained devices through a mobile application, through security in the cloud, such as secure device management throughout the device life cycle using DTLS. The factory configuration utility sets up your gateway for secure connection and communication with Pelion Device Management, which ensures Device Management can authenticate your devices when they attempt to connect to your account. You can even select the most suitable security framework for your needs, including secure hardware, selection of a certificate authority (CA) and factory-generated keys.
What Arm offers
Pelion Edge is part of the Arm Pelion platform, an end-to-end device management solution. This platform can solve your problems throughout the many steps of the device management journey. We can walk you through device onboarding and device connectivity and management, as well as data collection and management. We also offer commercial support to help debug and troubleshoot any issues you may face.