Overview
In this tutorial, you use the secure device access (SDA) software development kit (SDK), the SDA client SDK and a demo Android application to perform operations on a K64F device in a secure manner.
As part of the demo, you create two users that represent two technicians, each of whom belongs to a different user group and has permission to perform a different set of operations on the device.
The IoT device does not have access to the Device Management server, so the technicians connect to the device over USB.
Each technician connects to Device Management and requests an access token to perform specific operations on the device. Device Management provides an access token for the requested scope of operations or rejects the request based on the policies assigned to the user group to which the technician belongs.
Note: For more information about the SDA concepts referred to in this demo, see How SDA works.
The technician then attempts to connect to the device and perform operations. The device allows the technician to perform the requested operations or denies the request depending on whether:
- The device is part of the audience of devices the technician is allowed access to.
- The activity is within the scope of operations of the given token.
Demo participants
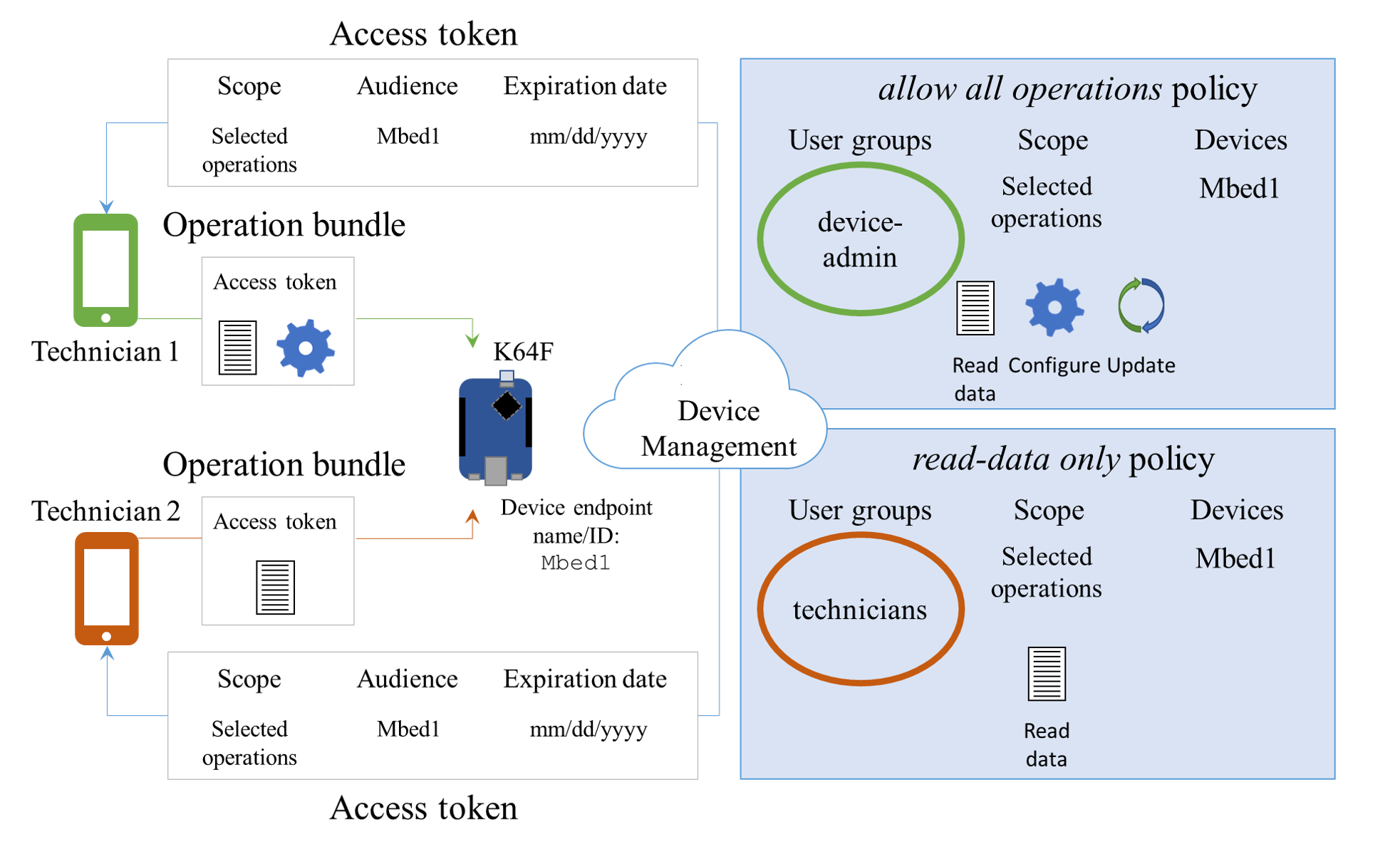
As shown in the diagram above, the SDA demo includes the following entities:
-
K64F - The device can perform the following operations:
- Read data - Read the temperature.
- Configure - Set a temperature threshold on the device.
- Update - Perform a 'firmware update'-like operation. To perform this operation, the technician must belong to the device-admin group.
-
Technician 1 - Belongs to the device admin user group, which has permission to perform all operations on the device.
-
Technician 2 - Belongs to the technicians user group, which is only allowed to perform read-data operations on the device.
Demo steps
The SDA demo tutorial takes you through all of the steps required to:
- Set up your Device Management account, including creating users, user groups and policies.
- Obtain a bootstrap certificate and trust anchor.
- Set up the SDA client on your IoT device.
- Set up the SDA SDK and demo application on your Android device.
- Connect your Android and IoT devices to each other over a serial connection and run a number of scenarios that demonstrate how the IoT device protects itself.